The Everlasting Hack
The easiest way around the law is to be the reason for the law.
Intro and recap
On September 11, 2001, the New York Stock Exchange and Nuclear Regulatory Commission shut their cyber systems down in the wake of the attacks on the World Trade Center.
NYSE, American Stock Exchange (AMEX), and NASDAQ all came back online on September 17, 2001, while the NRC restored theirs on September 18, 2001.
The same day the NRC restored their public-facing internet services, Carnegie Mellon University’s CERT Division reported the first advisory concerning the Windows-vector “Nimda” worm — The first backdoor-seeking computer worm known “in the wild”.
But it certainly wasn’t the first worm-virus to mysteriously appear from nowhere, and also wasn’t the first to be engineered to target and exploit Microsoft products.
R&D worms
Since around 1998, the progression of major computer “worms” have mirrored contemporary research in “wormhole computing” (early-1990s), which utilized “parallel processing” (mid-1990s) over “distributed networks” (late-1990s). This was known in the early days as “massively parallel architectures.”
With the progression of each successive attack since the MELISSA Virus, new concepts of technology then-under development were introduced and when assembled in hindsight, reveal the skeleton frameworks of what we now know as “remote diagnostics” and “automatic updates”.
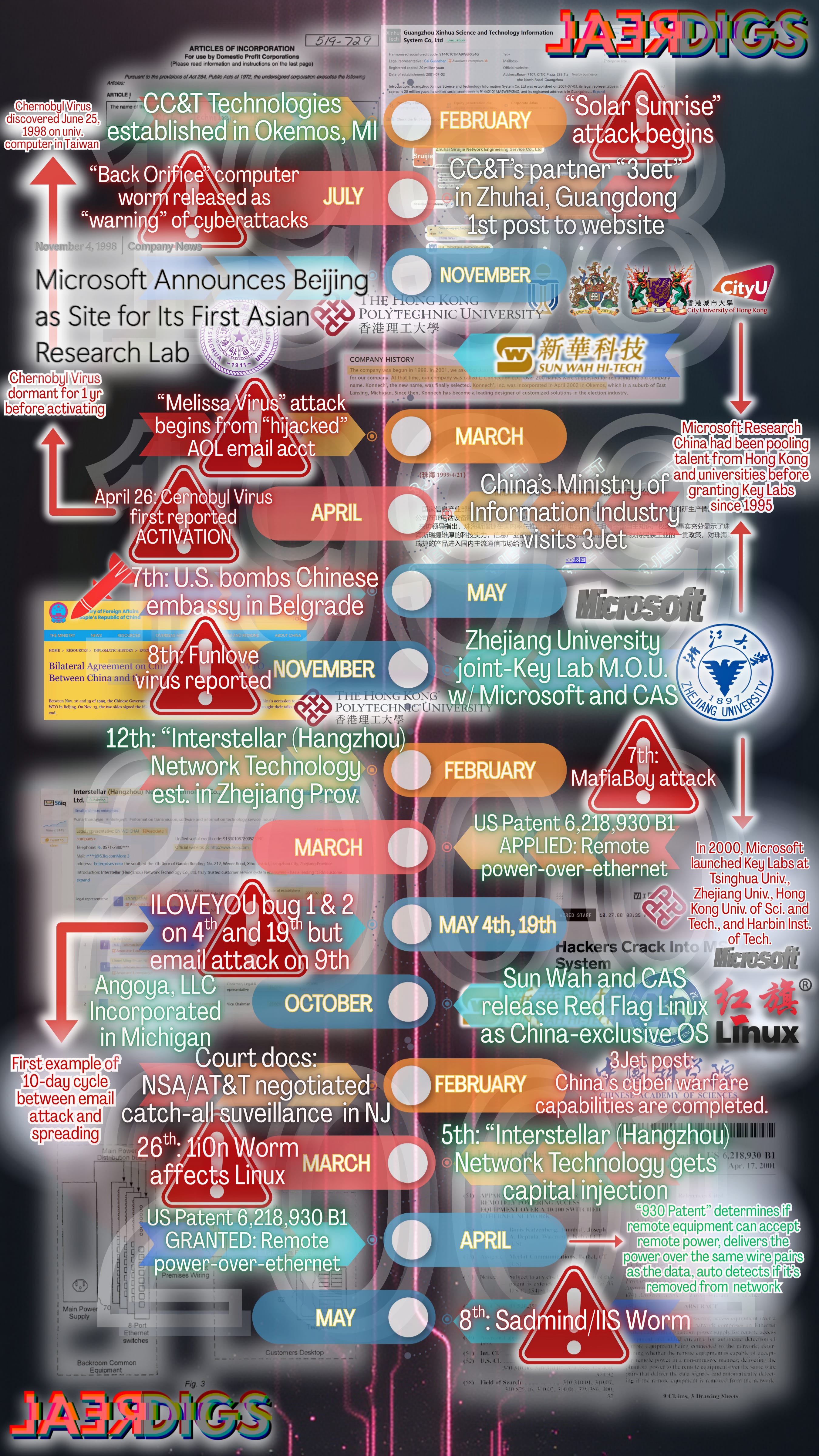
Microsoft swarms China
Zhejiang University was the first Microsoft joint-Key Lab inducted into the Microsoft Research Asia family in late 19991.
By the turn of the millennium, Zhejiang University, Hong Kong University of Science and Technology, and Hong Kong PolyU were all connected directly to Beijing and the Chinese Academy of Sciences by Microsoft Research Asia.
By the end of the year 2000, the partnerships formally reached Zhejiang and Tsinghua universities, Harbin Institute of Technology, and Hong Kong University of Science and Technology.
In short, by 1998, Microsoft and the Chinese Academy of Sciences were virtually synonymous when it came to “cloud”“ computing — or “massively parallel architectures”.
Microsoft pulls Hong Kong closer to Beijing
As a longstanding member within the various central civil functions of the Mainland Chinese government, Dr. Jonathan KS Choi has also long been a State-approved facilitator between financial markets, political power, academia, research and development, manufacturing, and shipping.
Y2K and beyond
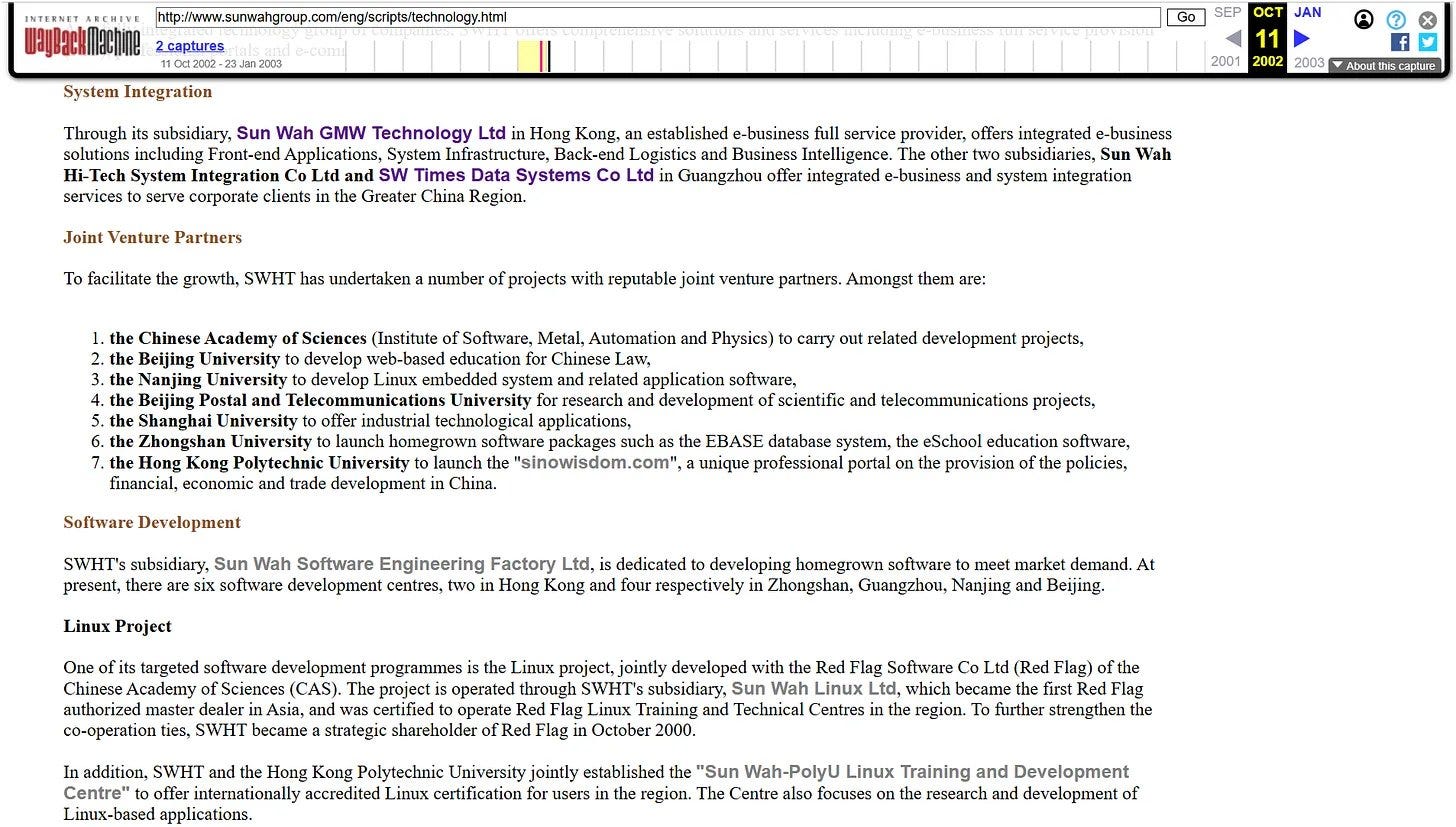
In 1998, Sun Wah Hi-Tech was established under the flagship Hong Kong-based Sun Wah Group, who was firmly rooted in Canada after buying the controlling stake of its own SW Kingsway Capital, also in 19982.
Sun Wah Hi-Tech was one early company to developing a web-compatible Chinese Unicode character system in 1998. Sun Wah Hi-Tech also launched an operating system for the Chinese Academy of Sciences in 20003.
The company was well-connected to the central government and the ruling Communist Party of China. Top brass of Peking University came to instruct Sun Wah on legal requirements and how to navigate American trade laws to Party standards in 19984.
Sun Wah Hi-Tech + Linux + Microsoft
In late 1999 and into 2000, Hong Kong Polytechnic University (PolyU) inked agreements with Sun Wah in October for a “Linux Training & Development Centre”, and with Microsoft China in November for, “academic research and exchange of research staff.”5
The title of the Hong Kong PolyU release was even “Partnering Sun Wah and Microsoft.”
The fork in the “X-road”
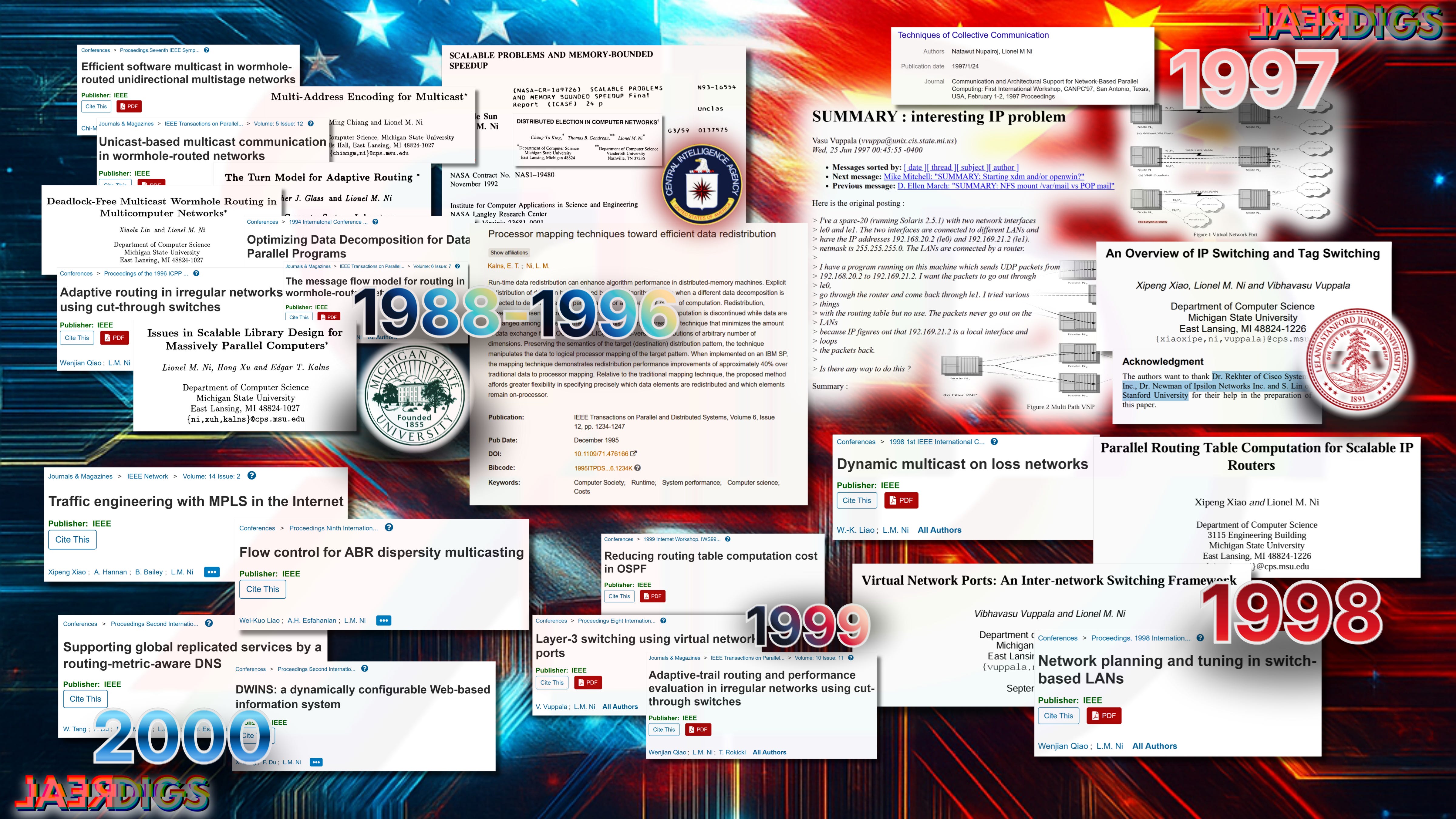
One professor’s name popped up time and time again with Michigan State University and “wormhole computing”, also with a Zhejiang University graduate and GlobalCenter employee named Xipeng Xiao who was studying to earn his 2000 PhD.
There were multiple instances in the acknowledgements of the research thanking individuals from Cisco Systems, Juniper Networks, and professors at Stanford University.
Xiao also appeared in documents and postings for Zhejiang University’s US-based alumni group.
Yadong Gui was another recurring name, historically6 throughout the literature, associated with the Institute of Computing Technology of the Chinese Academy of Sciences7.
Before Reddit…
On June 25, 1997, MSU grad student Vibhavasu Vuppala posted to a message board8 troubleshooting routing issues in a novel network scheme under development. That scheme was miniaturized and integrated into his PhD supervisor’s commercial product called an “internet emulator”.
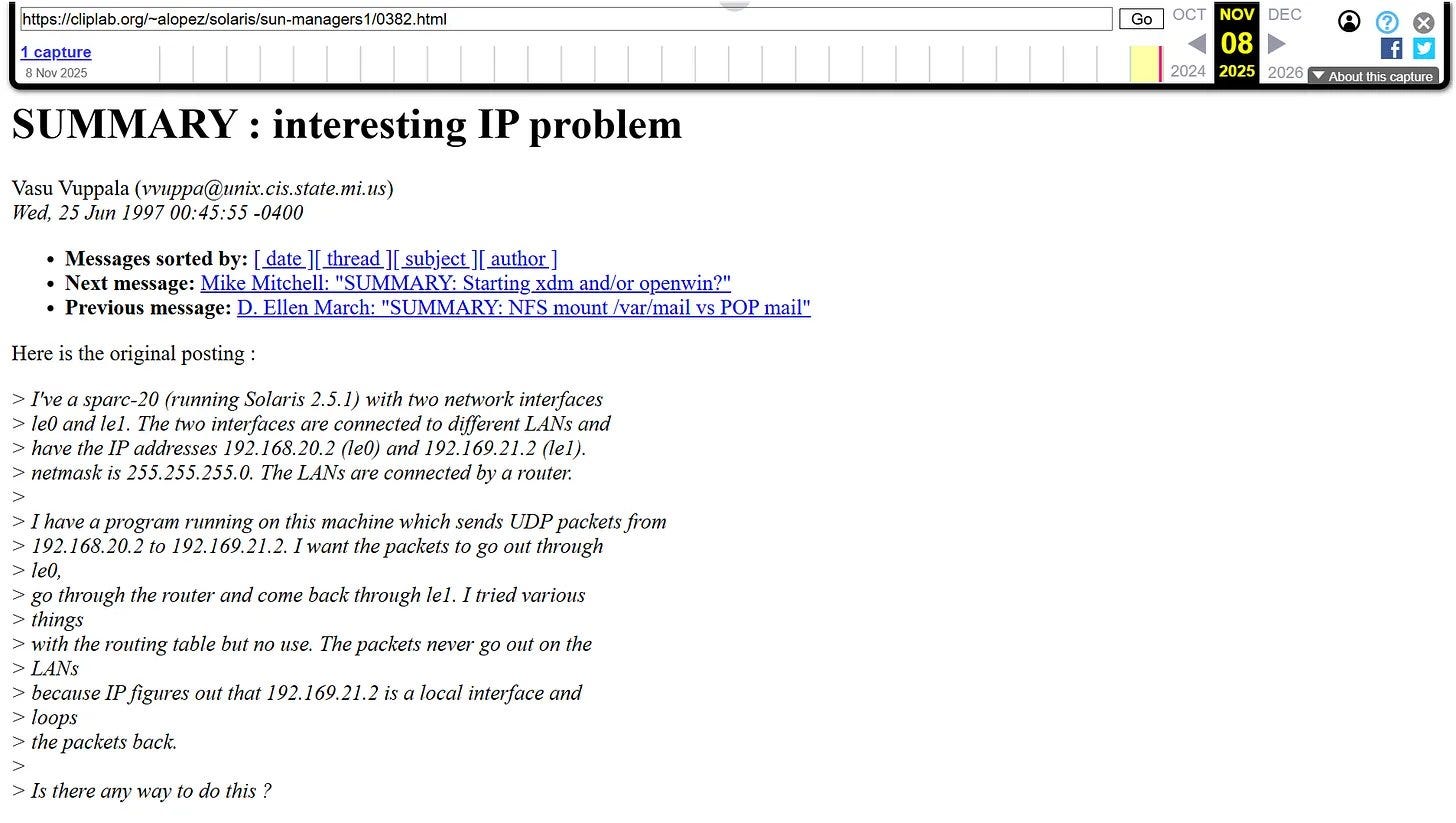
What may be the results of that very research were published the same year9 and in August, Vupalla and his PhD supervisor gave a seminar at a symposium on Design of a Scalable IP router10.
Vuppala even used similar IP addresses in testing to those he published in September 28, 199811 and in January of 199912.
Around July of 199813, technology aligning with these concepts appeared in a product called ‘EMIP-1,’ an onboard network diagnostics tool for VoIP, which was reportedly sold in July 1998 to China Aerospace Sanjiang Group Co., Ltd. (referred to as ‘3Jet’ in some contexts) (中国航天三江集团有限公司).
Sanjiang Space Industry Group14 is a “cousin” of the company, and is headquartered in Wuhan, Hubei Province, according to the Rand Corporation15. The Americanized name of this company was “3Jet Network Engineering & Service” in Zhuhai, Guangdong Province, China.
The endlessly versatile invention, the “EMIP-1” was sold in the 3Jet context as an onboard network diagnostics tool for VoIP systems (telephone via internet), but what the tool was actually capable of was so much more.
China follows through
Sometime between mid-October of 199816 and a February 2, 2001 Internet Archive capture, the Chinese government announced their preparations for cyberwarfare and “information warfare” had been completed17.
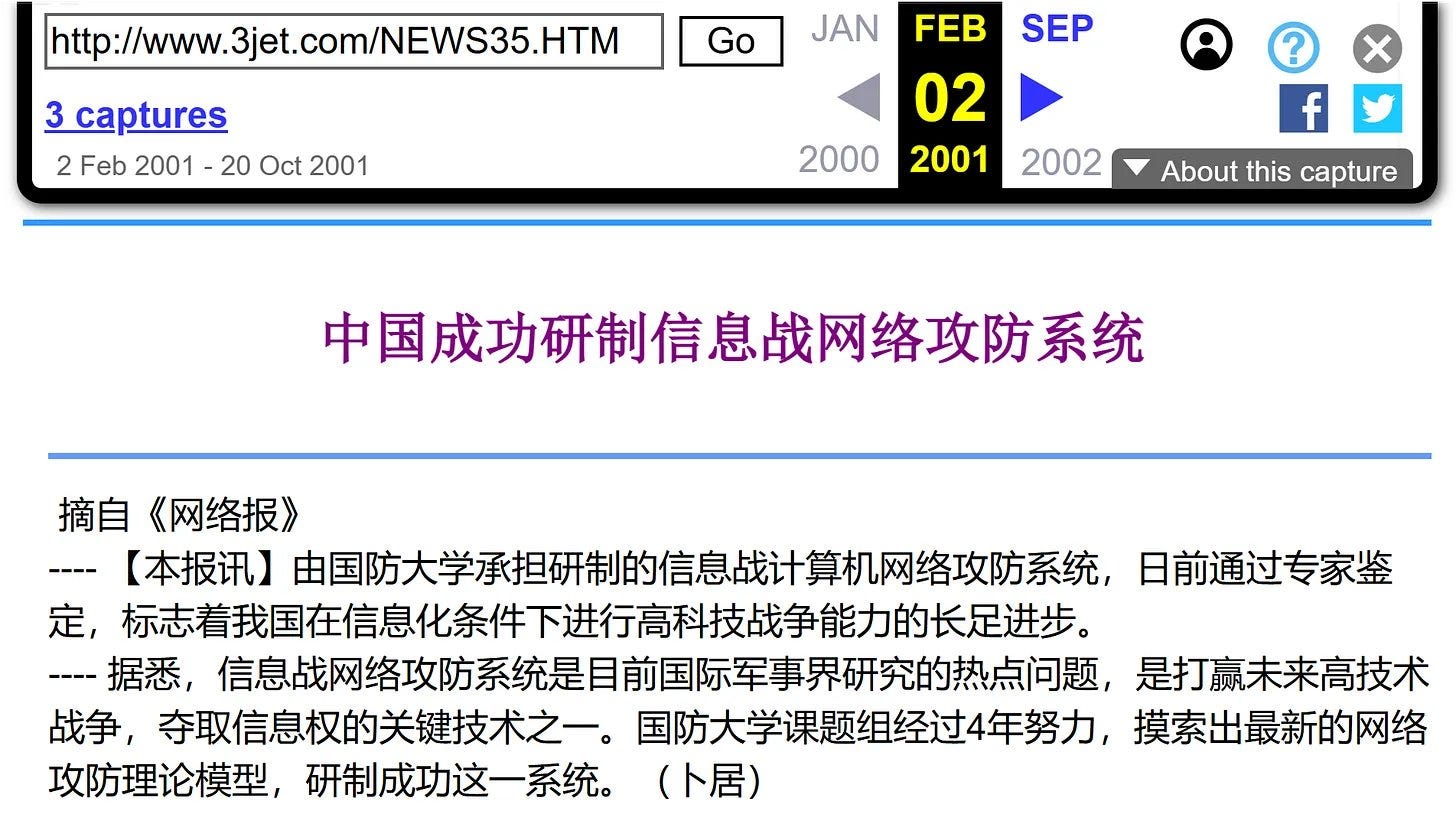
The 3JET entity announced on April 21, 1999 that leaders of the Ministry of Information Industry visited the company to review their products and work18.
On October 17th, the company received a visit from all the Deputy General Manager of China Sanjiang Aerospace Group, the Vice President of Harbin Institute of Technology and General Manager of Harbin Institute of Technology Group, putting the company directly in the view of the P.L.A. and central Chinese government19.
Harbin Institute of Technology went on to host one of the four formal Microsoft Key Labs founded in 2000.
Sometime before April 14, 2001, Okemos, Michigan-based CC&T Technologies, the partner of Sanjiang Aerospace Group, posted to their American-facing website that the EMIP-1 internet emulator was under review by the Chinese government20.
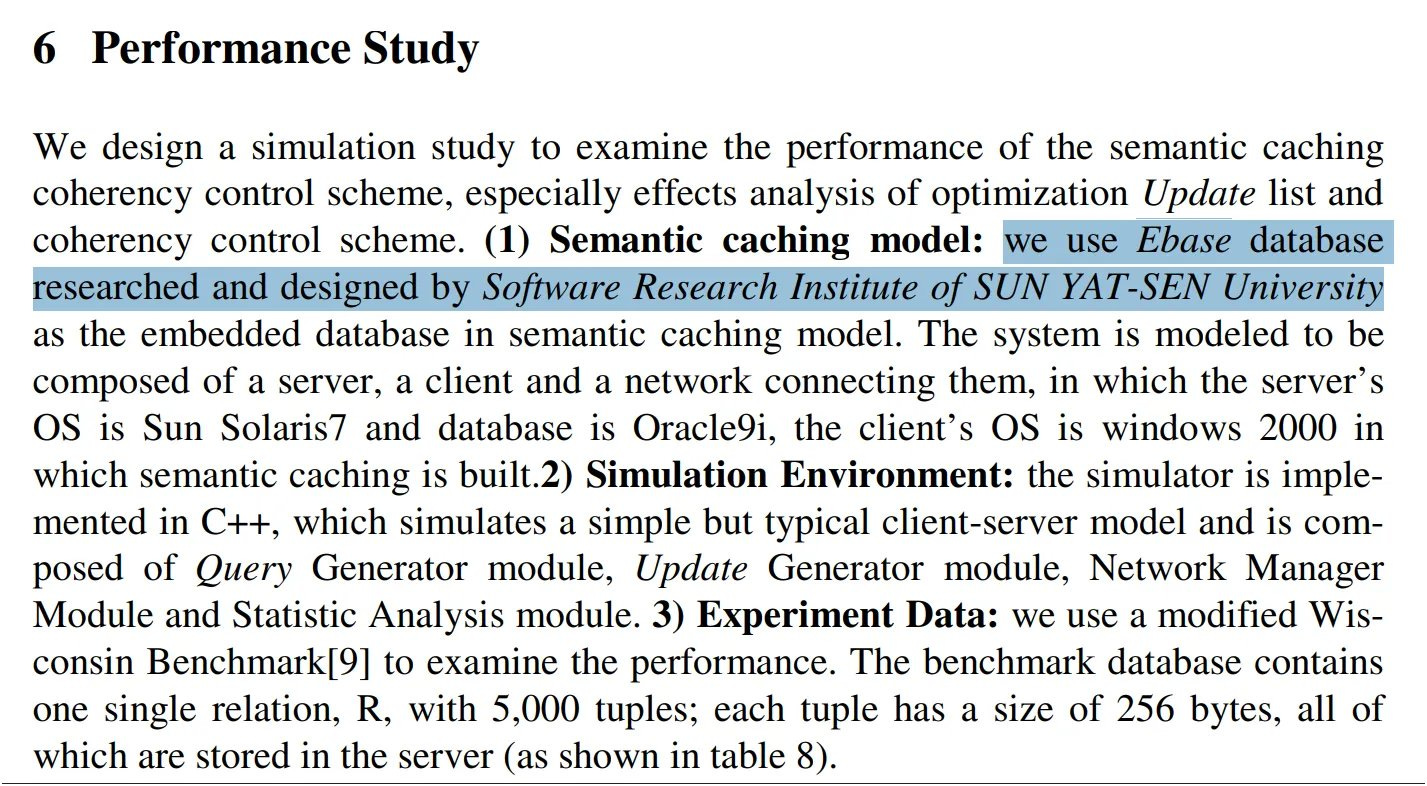
“eBase”
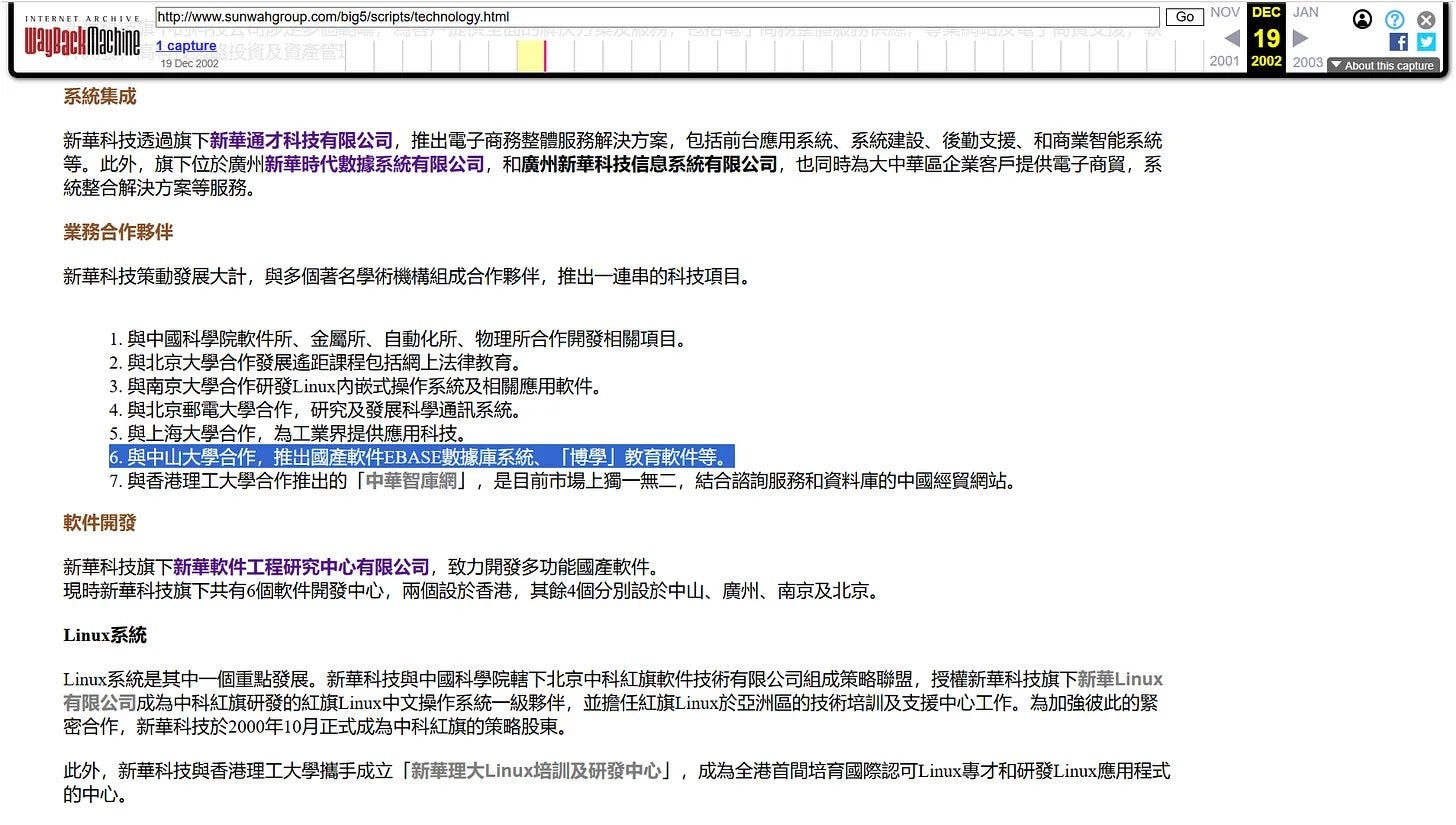
In 2005, Sun Yat-Sen University was employing a system known as the “eBase” database system21, which was also mentioned by Sun Wah Hi-Tech in 200222.
As a financial advisor to the Dean of the Chinese Academy of Sciences, Choi has an ear to the ground of global technological developments, even those not yet to market yet.
As a trustee of both Fudan University in Shanghai and Hong Kong University of Science and Technology (HKUST), Sun Wah also at that time enjoyed collaborative partnerships with the Chinese Academy of Sciences, Peking University, Nanjing University, Beijing University of Posts and Telecommunications, Shanghai University, Sun Yat-Sen University, and Hong Kong Polytechnic University (PolyU).
Historical hacks with academic origins?
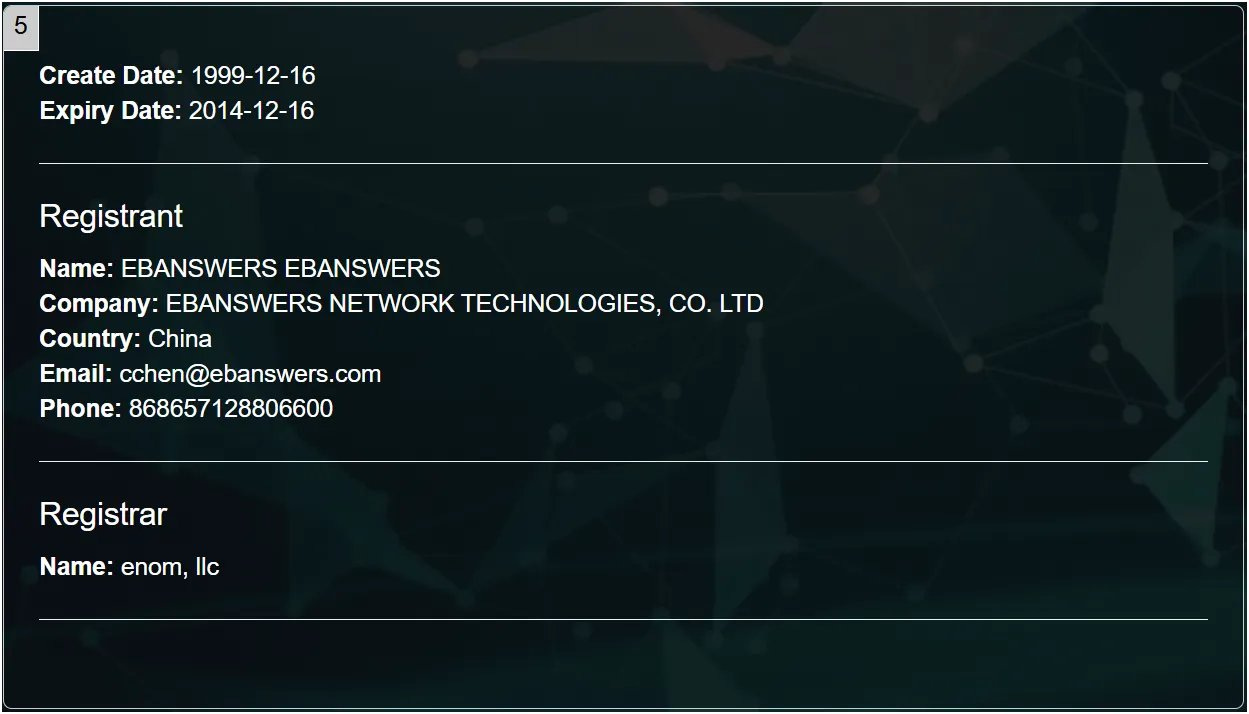
The chief pioneer of the technology discussed here began a Mainland China-based business called Interstellar (Hangzhou) Network Technology Co. in 2000, d.b.a. eBanswers — as in answers from the eBase.
Curiously, the domain ebanswers.com was registered nearly three months before the company was founded to Chen Chengqiang, indicating the continuity between 3Jet and Interstellar23.
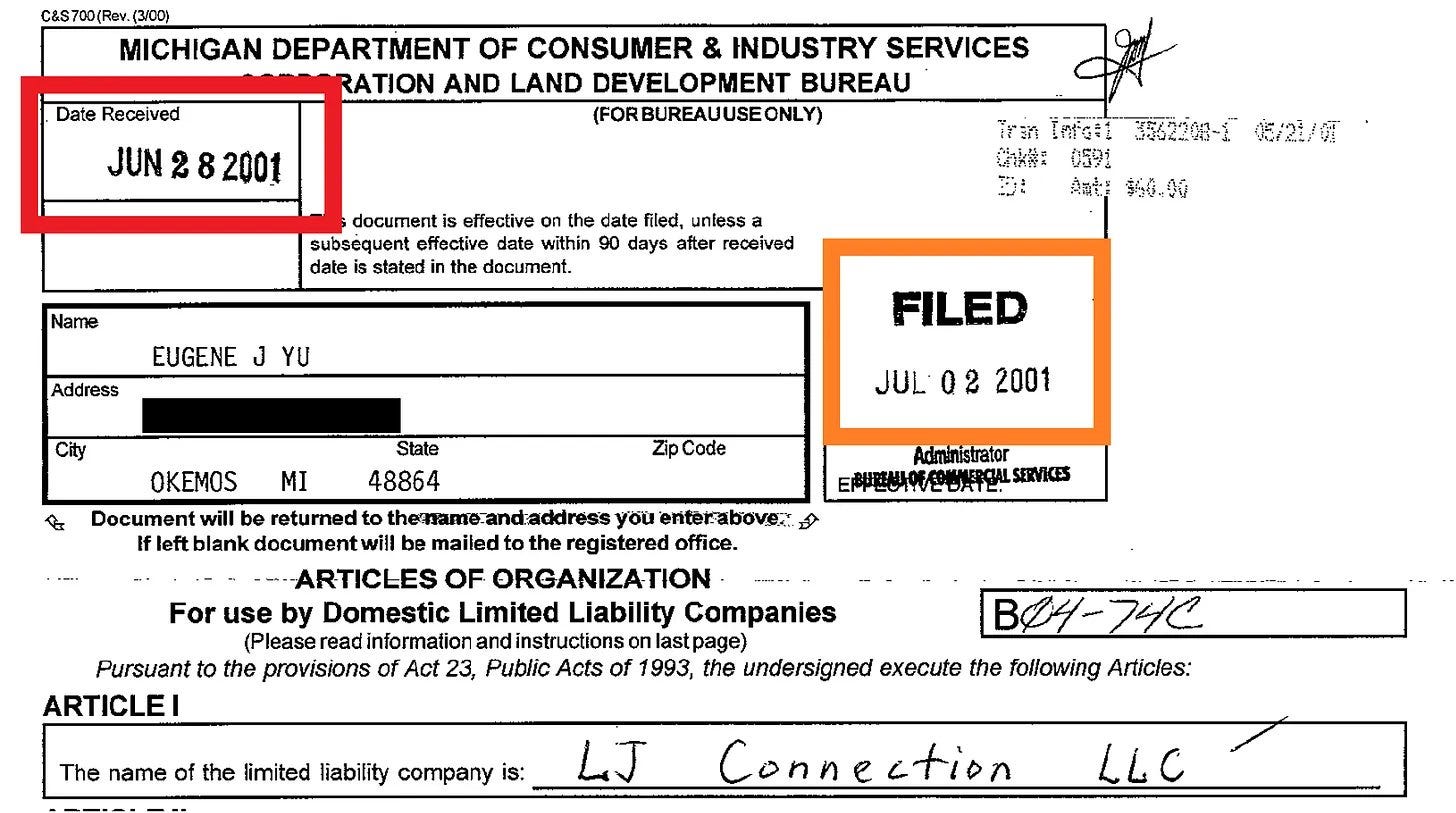
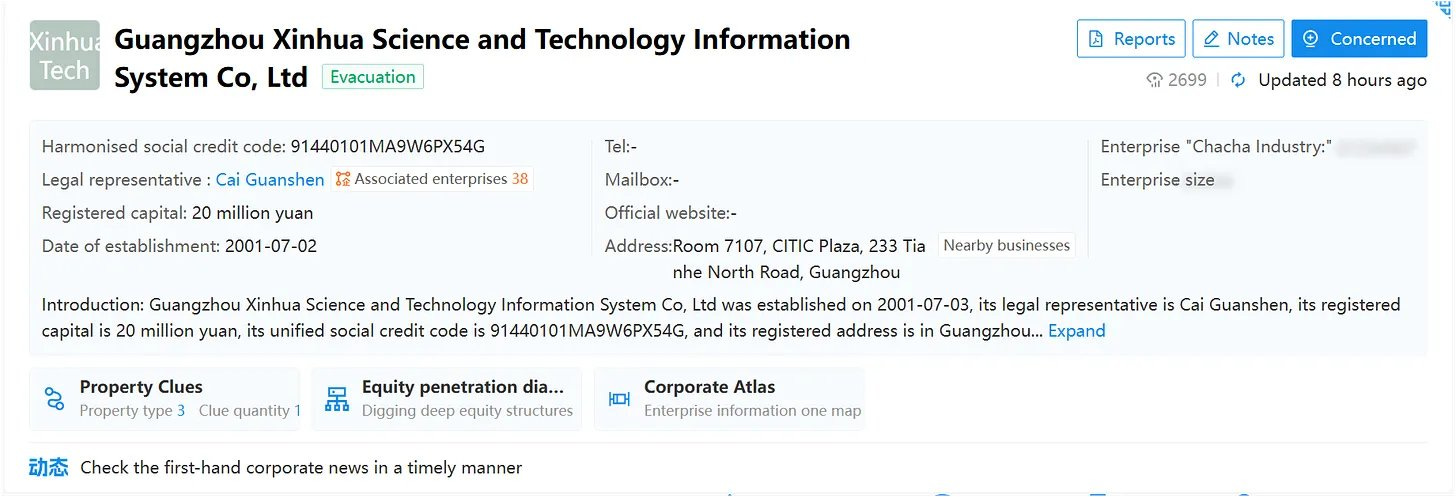
Sun Wah Group filed their tech subsidiary, Guangzhou Xinhua Technology Company, on Monday, July 2, 200124 — the very same day that Eugene Yu registered LJ Connection in Michigan. What’s more is that Sun Wah appears to have been monitoring the progress because the filing was actually received on Thursday, June 28th.
This body of evidence provides everything except the smoking gun of proof of the coordination between the inventor of the product and the Chinese government.
Severe case of TDS
Sun Wah Group also had under its umbrella a database company called SW Times Data Storage (or Sun Wah TDS) in 2001. Located in Guangzhou, Sun Wah TDS worked closely with Sun Yat-Sen University25.
Sun Wah TDS also provided satellite “intranet” — as troubleshot by Vasu Vappula from earlier — but facilitated live video uplinks26; Somewhat prescient of the CIA company Elemental’s 2018 “backdoors,” as reported by Bloomberg Businessweek27.
Interesting to note, this series of hacks, as well as many other historical “attacks” have occurred around the times of year of which Chinese university students are taking exams, or finalizing dissertations and thesis papers.
Recap and coming revelations
The 1i0n Worm, Sadmind/IIS, and Code Red worms were wrongfully implanted to access admin privileges later through repeated incursions later, opening backdoors for “wormhole routed computing.”
Even if not an attack originating from supposedly “friendly” entities, the concepts that these worms and viruses utilized managed to somehow make their way into the very fabric of daily computing done around the world.
From using “backdoors” to debug and troubleshoot systems, to “sniffers” to scour entire chunks of the internet for archival, and even automatic system updates, the “backdoors” mean the end of privacy.
Even in the near-certain event that the LJ Connection was only one link to more sinister plans, it was only one attack vector, and all that was needed to penetrate the American infrastructure once and for all.
Unfortunately, it wasn’t an isolated incident.
Maybe the tech industry shouldn’t have fought the “Clipper Chip” in the 1990s so hard after all...