What Does PollChief Have To Do With Me?
A story that isn't anything you clicked into this thinking about.
Imagine with me, if you can:
The year is 2022. Midterms are swiftly approaching with no shortage of nuclear-bomb-sized revelations of ever-growing scandals in the Department of Justice’s negligence and lop-sided application of justice to elections, insurrections, subversive attempts to overthrow duly elected government, social activism, kompromat, espionage, all continuing to pile onto the Bureau’s already speckled history.
Twenty-one months following the hotly contested 2020 Presidential election, there is still a growing collective of election skeptics.
So then why care about a small business that writes election management software?
For some insight, let’s shift focus momentarily.
Okta is a very successful company founded in 2009 with a reputation in secure data authentication. Their services are run exclusively on Amazon Web Services or AWS. AWS owns and operates massive data facilities globally that process an enormous swath of data on the internet as a whole.
Despite Okta’s wild success story, it has not come without their share of issues. They’ve experienced multiple data breaches in recent years, but have reported minimal setbacks and seem to have been able to respond to these incursions effectively.
Why bring Okta and their success in data authentication into a discussion about elections that many people still claim were corrupted by nefarious behavior? Not because of what you may think.
The Los Angeles County Registrar-Recorder/County Clerk website provides an election management system diagram that maps what appears to be a plan for implementing a future election system, based from the page’s title, “EMS Future State v15” found at:
This diagram, highlighted in yellow, shows “OKTA,” “PollChief,” “Data Integration,” and “County API Gateway”. In red, “EMS,” or Election Management System. Also note the legend in the bottom left corner and the color-coded representations displayed by the boxes in their diagram.
PollChief is the software developed by Konnech and covered in Kanekoa’s previous piece. All data processed through the whole of the Election Management System is routed through the PollChief software, which is subsequently sent to “OKTA” for “SSO” and “MFA” - “Single Sign-On” and “Multi-Factor Authentication” protocols.
While this is an authentication process that happens millions upon millions of times daily, it also lends an apprehension a bit above that of ordering overpriced, amber-colored Edison bulbs for the living room.
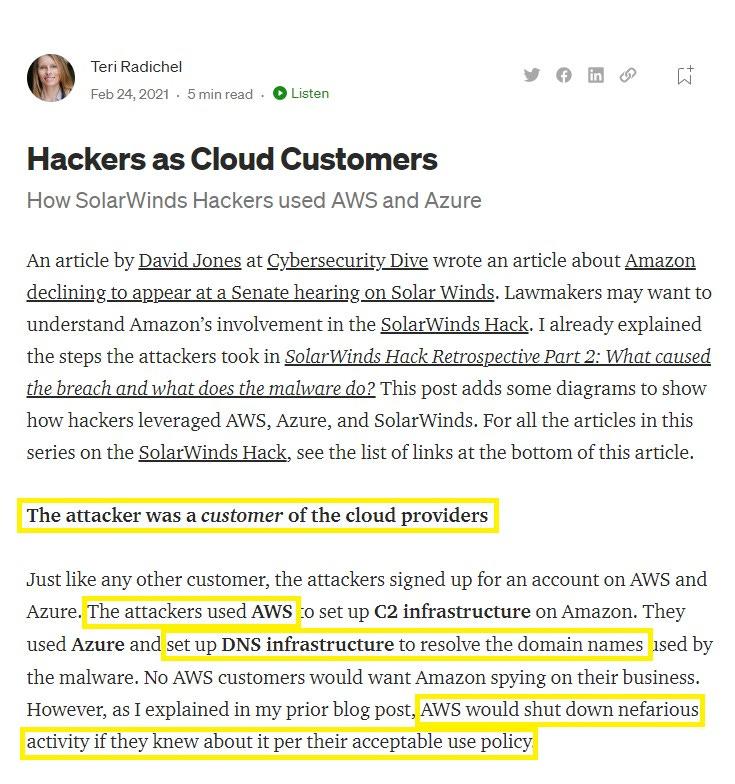
This offers a new lens through which to observe some notable hacks from recent history. The list is more extensive than I care to waste your time and my keyboard for, but I’ll leave an example of a very public one that occurred around the same general time as the 2020 elections. This breach also happened to a company that uses Amazon Web Services as does Okta (our focus today):
So now we have learned that a customer of AWS can set up a “backdoor” into anything also connected to AWS and implant code into already existing software gradually over time, making it virtually undetectable? Who else have we learned uses Amazon Web Services?
Correct. Okta.
Refer back to Los Angeles County, where Konnech’s “PollChief” software seems planned to be used in the future. If you notice “County API Gateway”, it would suggest that all of the data held by the County administration would be accessible through EMS, PollChief, all the way to the Okta data portal.
The portal uses AWS, which we previously established has been “backdoored” during the SolarWinds breach without any real intrusion into their software at once.
The real possibility exists, evidenced by the SolarWinds attack, for a complete compromise of every vote, poll worker and their personal data, and the whole of election procedure in general that would be managed using Okta authentication services, with or without any actual incursion into the system itself. This is a glaring vulnerability for normal, everyday Americans.
It leaves me with one nagging business question after learning all of this: If Okta has such a stranglehold in the data authentication industry, then who is their competition in such a seemingly niche service?
Answer: A Chinese company called Authing.
There have been multiple statements from state and federal officials addressing their investigations into the 2020 election and “unfounded” claims of digital manipulation.
Not one of those statements have approached acknowledging the existence of this vulnerability, of which most experts agree there is no guarantee of preventing.
Is it time for us to demand that the FBI disclose everything they found, being that they have consistently reported no areas of “legitimate concern”?
Is it time to demand that every group involved in our most sacred tradition — the cornerstone of “democracy” — tangibly prove to the American citizens that what happened to SolarWinds could and never did happen to our elections?
Much more to come…