The Wrong Place For Keys To The Kingdom
Some things aren't meant for the internet. Elections, sensitive government data, and personal information are all at the top of that list.
China Telecommunications Corporation
According to Wikipedia, China Telecommunications Corporation (CTC) is a state-owned telecom company headquartered both in Beijing and Shanghai, providing mainland China and the Philippines with internet and phone service. CTC has been a convoluted hodgepodge of acquisitions, mergers, and joint ventures between privately-owned but state-directed, and fully state-owned telecom companies since the 2000’s, including China Unicom.
China’s entire government apparatus operates as a unit under the firm grip of the Chinese Communist Party.
Prime subsidiary of CTC, China Telecom expanded globally in 2007, buying three companies: China Telecom System Integration, China Telecom Global, and China Telecom (Americas). Between 2012 and 2013, China Telecom (Europe) declared its intent to expand European and Asian access, and acquired a digital “trunking” business as well as China Telecom (Europe) from China Telecom Global in the “seventh acquisition” (page 134).
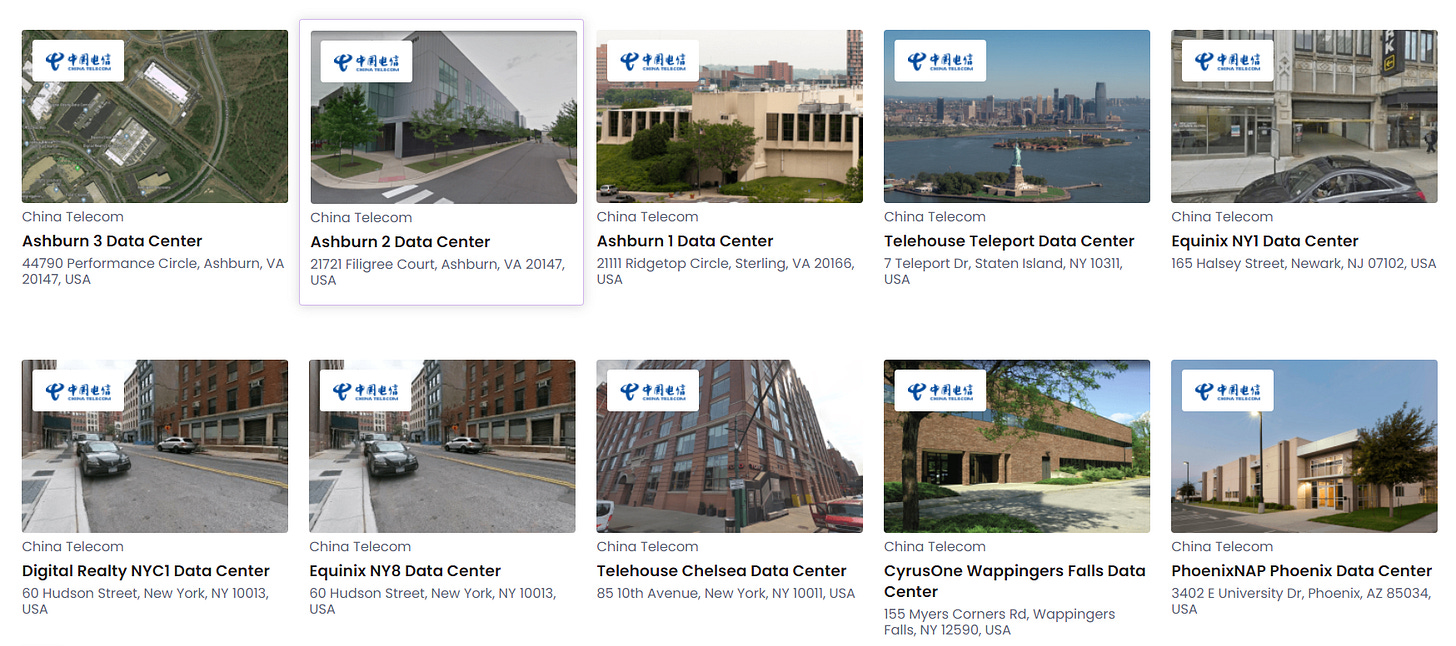
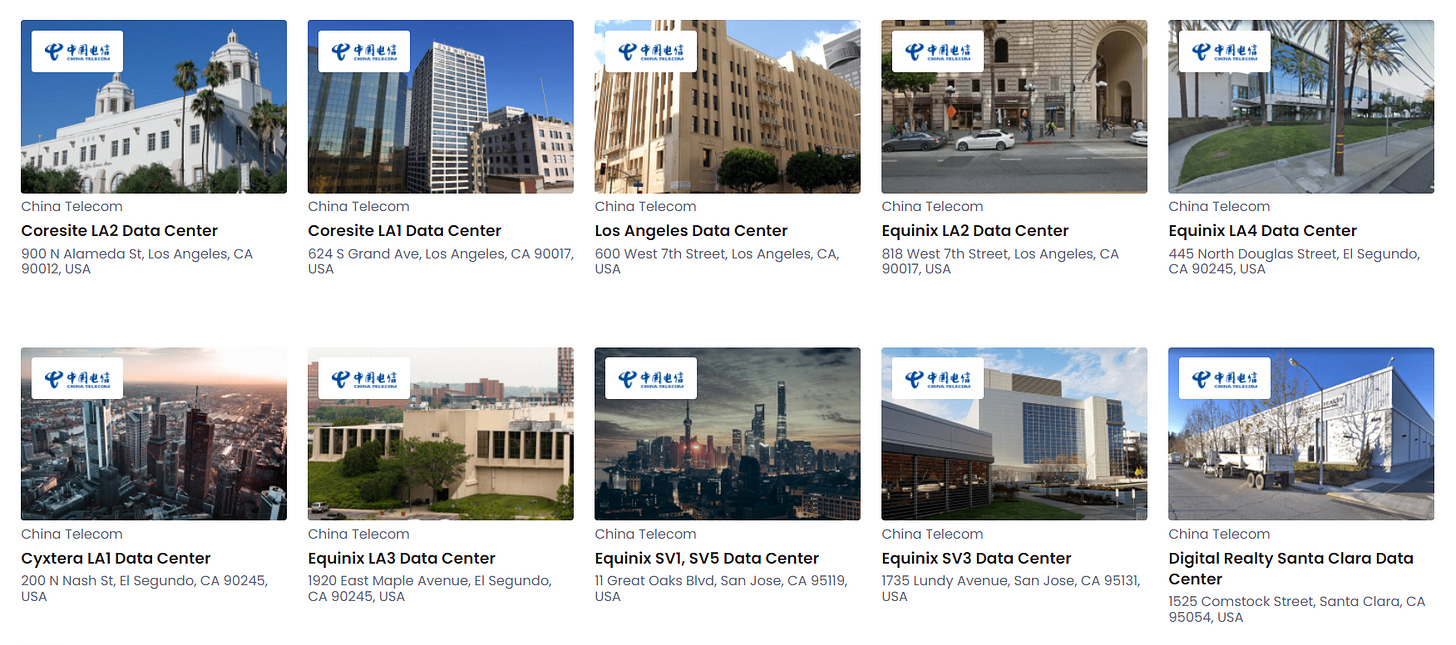
According to datacenters.com, China Telecom currently owns 24 data hubs in the continental US located in Ashland, VA (2), Sterling, VA, Staten Island, NY, New York City (3), Wappingers Falls, NY, Phoenix, AZ, Newark, NJ, Los Angeles, CA (4), El Segundo, CA (3), San Jose, CA (2), and Santa Clara, CA (5).
CERNET
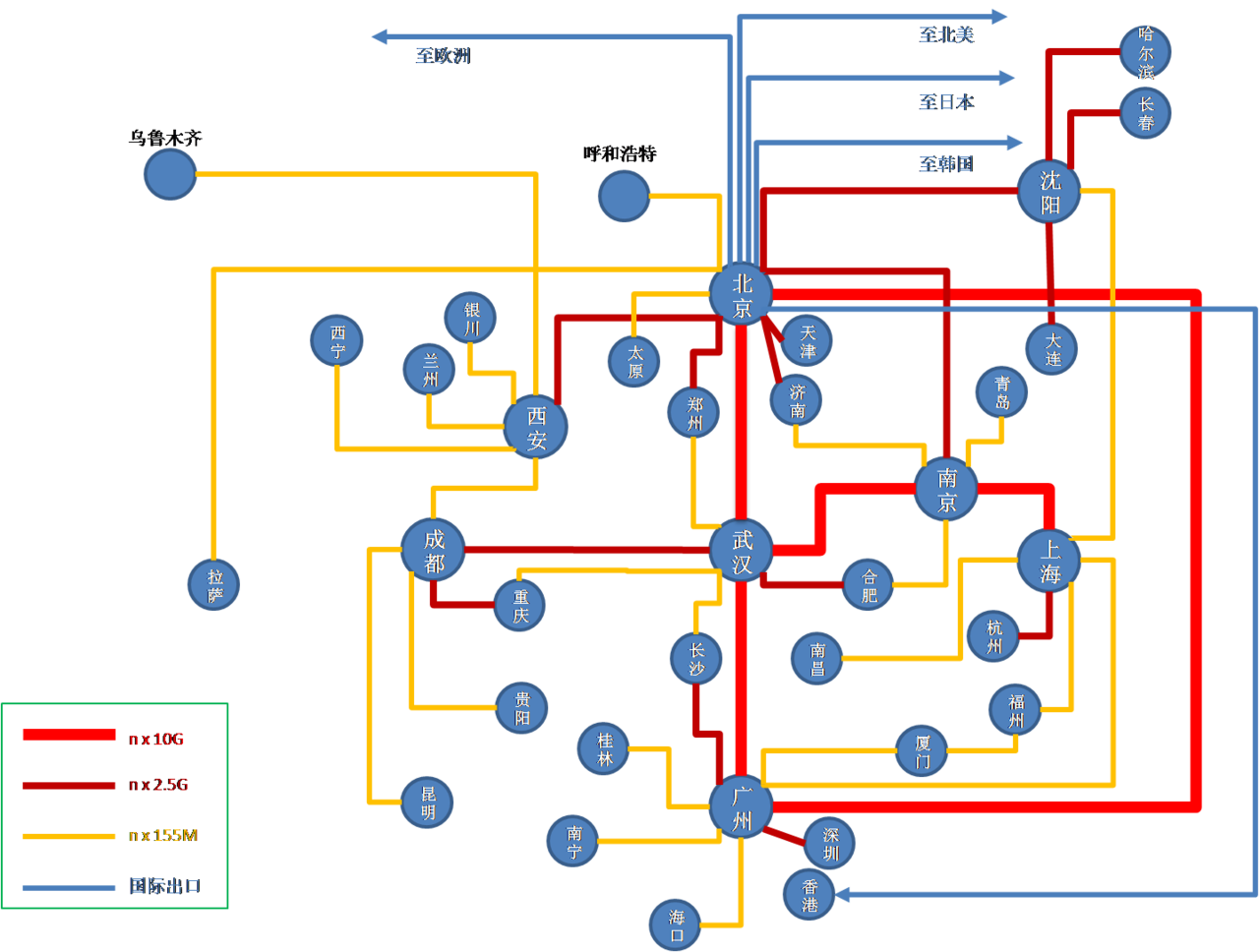
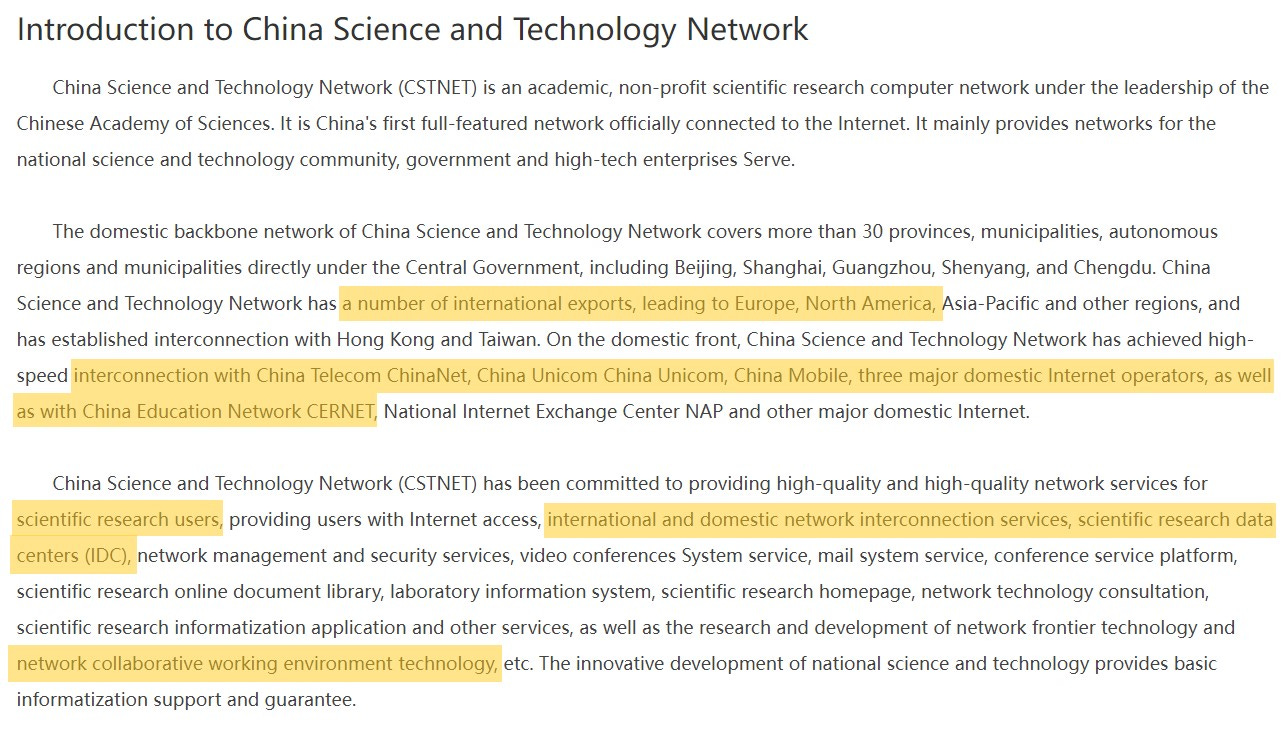
China Education and Research Network (CERNET) is a state-funded nationwide 100G, IPv6 network of over 20 million users constructed, operated, and managed by Tsinghua University in Beijing through the Ministry of Education of the People's Republic of China. It is comprised of four layers: the nationwide “backbone”, regional networks, provincial networks, and campus networks.
There are ten regional network centers with main nodes at Tsinghua University, Peking University, Beijing University of Posts and Telecommunications, Shanghai Jiaotong University, Xi'an Jiaotong University, Huazhong University of Science and Technology, South China Institute of Technology, University of Electronic Science and Technology of China, Southeast University and Northeast University. Each university is responsible for the operation, management, planning and construction of CERNET regional backbones.
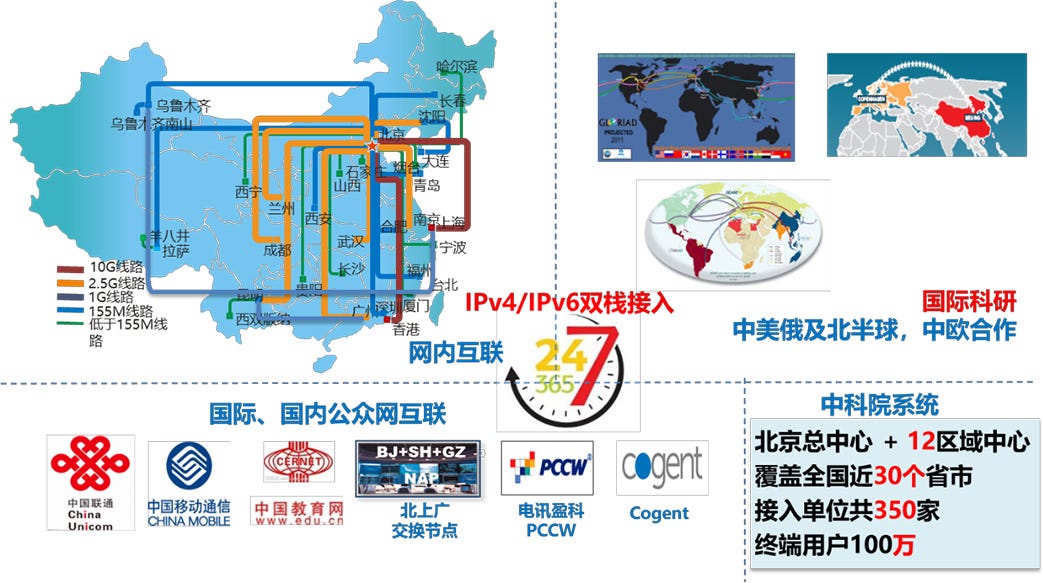
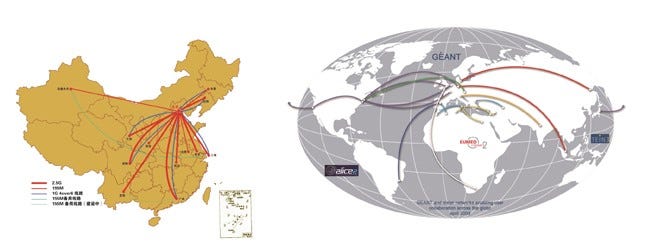
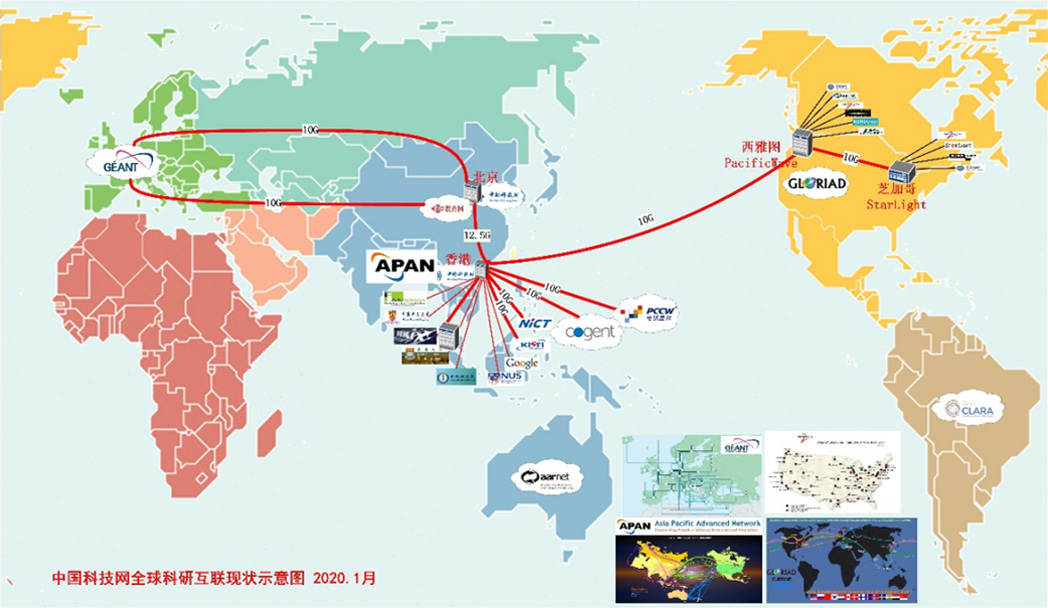
Both of these images can be found at https://www.cstnet.cn/runing
Before the advent of today’s CERNET, China Science and Technology Network (CSTNET) was launched 28 years ago on April 20, 1994 as the first directly-connected global internet provider in China. Now as an integral part of CERNET, CSTNET serves over 2,000 Chinese education, research, scientific and technical institutions, also providing network access, host trusteeship, virtual hosting, and domain registration to Chinese government bureaus and hi-tech industries. The Large Hadron Collider is also hard-wired into this network.
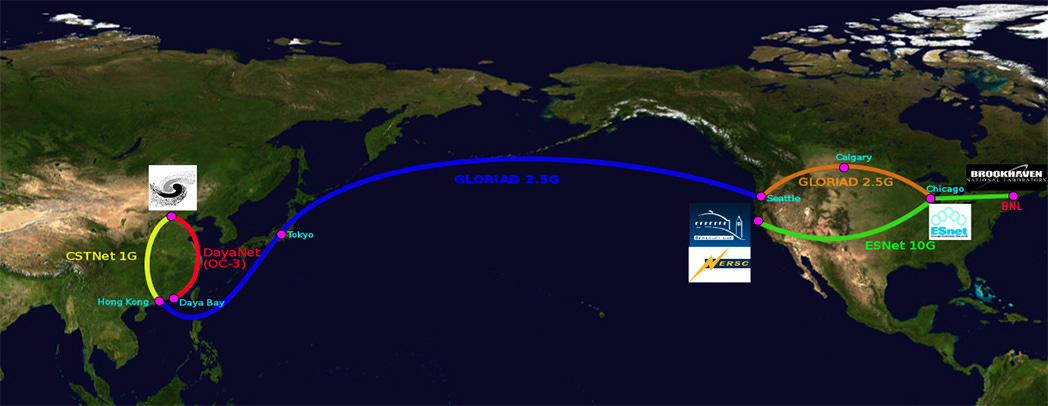
Below is a graphic provided by the CST itself, illustrating nodes in Seattle, Calgary, Chicago, New York, and San Francisco, also linked on the “Global Ring Network for Advanced Application Development”, or GLORIAD. GLORIAD ended formal operation in April 2016.
Chinese state-owned CTC now operates two direct connections between the U.S. and mainland China in consortium with other providers: the Trans-Pacific Express and the New Cross Pacific Cable System.
CERNET and the CCP’s Global Influence
As a partner of CERNET, Open University of China (OUC) serves as an inclusive education system to import and export minds from all over the world. Just as CSTNET and CERNET, the OUC also operates under the mandate of the Ministry of Education. OUC have historically partnered closely with the controversial Confucius Institutes all over the world.
On a 2015 archived webpage, the site announces, “The OUC undertakes work as a Confucius Institute’s Chinese partner institute [sic], and as such is responsible for selecting and dispatching excellent Chinese teachers to work at Confucius Institutes abroad...” [Search the entire list of Confucius Institutes here].
The Confucius Institutes, like all influential bodies inside China are under direct control of the Chinese Communist Party and by default, the People’s Liberation Army (PLA).
All the way through 2020, The Open University of China’s online list of university-partners included institutions like Peking University, Tsinghua University, Zhejiang University, Wuhan University, and Sun Yat-sen University. Among the list of international partners is Michigan State University in East Lansing, Michigan. The website did bear a copyright of 2009.
A swell of controversy over the Confucius Institutes in the mid-2010's made ample room for the Chinese Students and Scholars Association, or CSSA to grow their foothold inside the States in carrying out these same objectives.
Just as many other universities around the world, Michigan State offers a “Domains Initiative” — providing network access, hosting, and domain registration to, “…faculty, staff, specialists, and graduate students from across Michigan State University. It is a university-wide endeavor, led by the College of Arts and Letters, bringing together a growing number of partnerships, including with the College of Natural Sciences, College of Education, the Hub, Academic Advancement Network, Communication and Brand Strategy, and University Outreach and Engagement.”
Michigan State’s storied and extensive cooperation with CCP/PLA-sponsored initiatives to share students, teachers, and technology presents enormous security vulnerabilities systemwide. Whether from Michigan State or anywhere else, a CCP-commissioned student or faculty member with intimate knowledge of American and Chinese data systems creates an obvious national security conflict, electronic elections included — where elections intersect technology.
As for China, the government of the People’s Republic of China owns all internet traffic inside their borders or transmitted with their property.
U.S. Recognizes Chinese Cyberthreat
A 2010 article from Wired.com reported that for two hours, all Google internet traffic was rerouted through China and Russia with a headline, “Google Internet Traffic Wasn't Hijacked, But It Was Out of Control.” The incident was not an incursion in nature, but a programming mistake that created ISP routing errors.
With incidents like this in mind alongside the undetectable SolarWinds attack realized mere weeks prior, President Trump signed Executive Order #13959, “Executive Order on Addressing the Threat from Securities Investments that Finance Communist Chinese Military Companies” on November 11, 2020.
The order prohibited all U.S. investments in securities of companies identified by the U.S. Government as directly supporting the military of the People’s Republic of China. It was signed amid allegations of faulty internet-connected machines and potential international nefarious activity, as exhibited in the 2016 elections.
The allegations were met with no active response beyond vague official statements, censorship, and derogatory rhetoric in the public square. The refusal to acknowledge or investigate these claims would eventually be considered by the Department of Justice to be the basis of the January 6th riots on Capitol Hill. The USDOJ continues to label purveyors of these claims as “radicalized” and “extremists.”
On January 13, 2021, two days after EO #13959 went into effect, Trump signed Executive Order #13974 further clarifying the prior, and specifically included subsidiaries of the targeted companies, including China Unicom, as it operates in tandem with the CCP.
These companies included China Mobile, China Telecom and China Unicom — all of which were delisted by the New York Stock Exchange on March 9, 2021. Biden’s June 3, 2021 Executive Order #14032 went into effect on August 2, 2021. The order technically widened the scope of Trump EO’s #13959 and #13974, while critics argue it rendered Trump’s EO’s effectively inert.
The FCC revoked China Telecom and Unicom’s licenses to operate in America in late October 2021. They asserted that the Chinese tech giant, “is subject to exploitation, influence and control by the Chinese government and is highly likely to be forced to comply with Chinese government requests without sufficient legal procedures subject to independent judicial oversight.
They specifically added that China Telecom “raise significant national security and law enforcement risks by providing opportunities…” for the CCP "…to access, store, disrupt and/or misroute U.S. communications.”
On December 22, 2021, Reuters published the article, “China Telecom plans to continue some U.S. services after FCC revokes authorization.” Despite Executive action, the Chinese remained resolute in maintaining their direct network of connectivity with the rest of the globe.
These executive actions have not seemed to deter the Chinese nor inspire heightened urgency on behalf of the U.S. Government to protect American IT infrastructure from foreign malfeasance. This is clearly evidenced by the USIC and FBI’s collectively anemic response to the SolarWinds attack just weeks before [list of recent cyberattacks here].
China Telecom purportedly ceased operations in America as of January 2022. China Telecom continues to have access physical infrastructure, however it remains unclear to what extent China Telecom may or may not operate in America.
The Predicament
Any solution to the problem of being interconnected with the mortal enemies of liberty (the Chinese Communist Party) cannot include to simply disconnect from them. As will be evident in the next installment, Chinese and American corporations are already inextricably linked. Of itself, this isn’t necessarily negative.
The Sino-American relationship feeds off of the other’s development — enemies or not. When it comes to sensitive information including government or election data, there are already methods to protect it — closed networks, paper records, anything outside of placing our data on their networks in part or in whole, whether by intent or by accident.
Of big data companies since 2014, they have moved to a global model through massive venture capital funds, blurring the digital lines most notably between the Americas, Europe, and the Pacific.
It has become a symbiotic relationship economically and technologically, but under Chinese internet laws and by the CCP stance toward the US, raises enormous concerns of sensitive data harvesting, intellectual property theft, trade or state secrets, and more.
The crisscrossing webs of massive venture capital funds built the global systems relied upon by the developed world to function at a fundamental level. These funds have also funded some of the globe’s darkest players. Because these initiatives were woven together at their inception, the results will inevitably prove to be as well.